|


"GCHQ has
conducted mass interception of communications data from the world underwater
fiber-optic cables.
Under the program name Tempora, the GCHQ
developed the "ability to tap into and store huge volumes of data drawn from
fiber-optic cables for up to 30 days so that it can be sifted and analyzed,"
the Guardian reported, and the 'GCHQ and the NSA are consequently able to
access and process vast quantities of communications between entirely innocent
people.'
The intercepted data encompass all forms of online activity,
including "recordings of phone calls, the content of email messages, entries on
Facebook and the history of any internet user access to websites."
The
GCHQ's surveillance activities are every bit as comprehensive and
unaccountable-as the NSAs.
The sheer scale of the agency's ambition is
reflected in the titles of its two principal components: Mastering the Internet
and Global Telecoms Exploitation." - Glenn Greenwald

1979 Smith v. Maryland, 442 US
735
Telephone company, at police request, install on the central
switchboard a pen register to record numbers dialed from the telephone at
Smith's home.
A pen register, or dialed number recorder (DNR), is an
electronic device that records numbers called from a particular telephone line.
Petitioner moved to suppress "all fruits derived from" the pen
register.
The Maryland trial court denied this motion, holding that the
warrantless installation of the pen register did not violate the Fourth
Amendment.
Petitioner was convicted, and the Maryland Court of
Appeals affirmed.
Held: The installation and use of the pen
register was not a "search" within the meaning of the Fourth Amendment, and hence no warrant
was required.
Legalese allows inclusion of any device or program that
performs similar functions to the original pen register, including
monitoring programs.
March 22,
2000 Mark Lombardi is
found dead by hanging in his apartment shortly before an exposition. Found
drawings are illigible.
Mark Lombardi began in the early 1990s
researching the BCCI scandal,
the Harken Energy scandal, and
the Savings and Loan
debacle.
He noted information about the scandals on 3 x 5 note cards
and arranged the note cards into a framework of social network analysis which
he penciled as a diagram or bubble flow chart.
Lombardi called his diagrams Narrative
Structures.
He added research into
Houston S&L scandal - which Pete Brewton alleged the
Bush family, CIA associates and Mafia were involved -
Iran Contra scandal and
Adnan Khashoggi.
In 1999 Lombardi drew
"George W Bush, Harken Energy, and Jackson Stephens, ca 1979–90" shows
connections between James Bath, the Bush and bin Laden families, and business
deals in Texas and around the world.
June 2010
Swedish-born scholar and activist
Lisbet
Rausing publishes a widely-circulated essay in the journal
openDemocracy arguing for open access to scholarly articles.
She
specifically mentions JSTOR: "It is equally problematic that JSTOR, the
splendid 1997 database of most twentieth-century scholarly articles in the
social sciences and humanities, is off-limits for the public.
Look at
JSTOR (if you can).
There you find the evidence-based,
source-critical
foundations of sociology, anthropology,
geography,
history,
philosophy,
classics,
Oriental studies,
theology,
musicology,
history of technology and so on.
They are all closed to the public."
By the time of his death in
August 2019, Forbes estimated the net worth of Hans Anders Rausing, a Swedish
industrialist based in the UK, and his family to be $12 billion.
Hans
Rausing and his wife Märit Rausing had two daughters, Lisbet and Sigrid,
and one son, Hans Kristian Rausing.
"Not long after this,
George Soros Open Society
Foundations attempted to join forces with Rausing' Arcadia Fund to
make JSTOR widely available to the public, and Swartz kept up with these
efforts." - Noam Scheiber
[Noam Scheiber, Truman and Rhodes Scholar with
a master's degree in economics from Oxford University, is a
New York Times writer
and a former senior editor for The New
Republic.]
2011
Analysts are told they can
trace contacts of Americans as long as they cite a foreign intelligence
justification.
The NSA is exploiting huge collections of data to create
sophisticated graphs of Americans social connections to identify associates,
locations at certain times, traveling companions and other pertinent
information.
The agency is authorized to conduct "large-scale graph
analysis on very large sets of communications metadata without having to check
foreignness" of every e-mail address, phone number or other
identifier.
The agency augments the communications data with material
from public, commercial and other sources, including bank codes, insurance
information, Facebook profiles, passenger manifests, voter registration rolls,
GPS location information, as well as property records and unspecified tax data.
There is no restrictions on the use of "enrichment" data, and several
former senior Obama administration officials said the agency drew on it for
both Americans and foreigners.
The Justice Department and the
Pentagon decide it is
permissible to create contact chains using Americans' "metadata," which
includes the timing, location and other details of calls and e-mails.
The agency, citing Smith v. Maryland, 442 US 735,
claims it is not required to seek
warrants from the Foreign Intelligence Surveillance Court.
Smith v. Maryland Does Not Permit Mass
Surveillance
Phone and
e-mail logs allow
analysts to identify associates,
detect movement through time,
acquire affiliations, pick up sensitive information,
calls to Charles,
late-night extramarital partners
or exchanges with a
fellow plotter.
"Metadata can be very revealing.
Knowing the
number someone just dialed or the location of the person's cellphone is going
to allow assembly of a picture of what someone is up to.
It's the
digital equivalent of tailing a suspect." - Orin S. Kerr
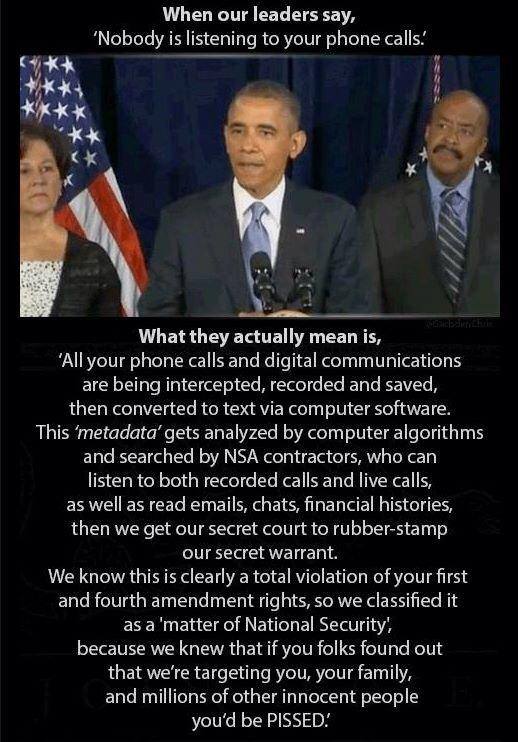
The policy - Defense
Supplemental Procedures Governing Communications Metadata Analysis -
was authorized by Defense Secretary Robert M. Gates and
Attorney General Michael B.
Mukasey.
"Sigint Management Directive 424", stated the
Supreme Court ruled
metadata was not constitutionally protected and allowed
collection.
Analysts, using metadata "without regard to the nationality
or location of the communicants" acquire the conversations of foreign
politicians, business figures or activists and anyone else in the
chain.
One of the main tools used for chaining phone numbers and e-mail
addresses has the code name Mainway.
Vast amounts of data flow
daily from fiber-optic cables, corporate partners and foreign computer networks
that have been hacked.
"Better
Person Centric Analysis" describes how the agency looks for 94 "entity
types," including phone numbers, e-mail addresses and IP addresses.
The
NSA correlates 164 "relationship types" to
build social networks and
what the agency calls "community of interest" profiles, using queries like
"travelsWith, hasFather, sentForumMessage, employs."


January 11, 2013
Aaron Swartz is found dead from
hanging in his apartment in New York.
Aaron was
accused of infiltrating
computers for the release of copyrighted academic articles and could have been
sentenced to 35 years in prison.
At 14 Aaron coauthored RSS (Really
Simple Syndication).
"The idea of sharing culture, knowledge and
information was from that very moment present in the actions of the young
Aaron, who combined a great
passion for freedom with
a refined expertise for
the development of collaborative network solutions." - Sérgio Amadeu
da Silveira
The federal indictment states matter-of-factly that "Swartz
intended to distribute a significant portion of JSTOR' archive."
The only real evidence of a motive or plan that prosecutors disclosed
was a document written in July 2008 called the "Guerilla Open Access Manifesto."
Swartz began
that widely reported post by arguing that, "Information is power. But like
all power, there are those who
want to keep it for themselves."


"Cyberspace favors
offensive operations.
These operations will deny, degrade, disrupt, and
deceive an adversary.
Cyberspace offensive operations ensure friendly
freedom of action in cyberspace while denying that same freedom to our
adversaries.
We will enhance our capabilities to conduct electronic
systems attack, electromagnetic systems
interdiction, network attack, and
infrastructure attack operations.
Targets include
the adversary's terrestrial, airborne, and space
networks, electronic
network attack systems, and
the adversary
itself.
As an adversary becomes dependent on cyberspace, offensive
operations have the potential to produce greater effects." -
Air Force Cyber
Command
"CYBERCOM will reach initial operating capability not later
than October 2009 and full operating capability not later than October
2010.
Ostensibly launched to protect military networks against malicious
cyberattacks, CYBERCOM's offensive nature is underlined by its role as
STRATCOM's operational
cyber wing.
In addition to a defensive hardening of the "dot-mil"
domain, the Pentagon plan calls for an offensive capacity, one that will deploy
cyber weapons against the adversaries of
neofeudalism/neoliberism/neoconservatism.
One
of ten
Unified Combatant Commands,
STRATCOM is the
successor organization to
Strategic Air Command.
Charged with
military satellites,
information
warfare, strategic
deterrence, global command and
control, intelligence,
surveillance and
reconnaissance, it should be apparent that designating CYBERCOM a STRATCOM
branch all but guarantees an
aggressive posture." -
Tom Burghardt July 1, 2009

 |
|
 |
This web site is not a commercial web site and
is presented for educational purposes only.

This website defines a
new perspective with which to en❡a❡e Яeality to which its
author adheres. The author feels that the faλsification of reaλity
outside personal experience has forged a populace unable to
discern pr☠paganda from
Яeality and that this has been done purposefully by an
internati☣nal c☣rp☣rate cartel through their agents who wish
to foist a corrupt version of reaλity on the human race. Religi☯us
int☯lerance ☯ccurs when any group refuses to tolerate
religi☯us practices, religi☸us beliefs or persons due to their
religious ideology. This web site marks the founding of a system of
philºsºphy nªmed The Mŷsterŷ of the Lumière
Infinie - a ra☨ional gnos☨ic mys☨ery re☦igion based on
reaso🐍 which requires no leap of faith, accepts no tithes, has no
supreme leader, no church buildings and in which each and every individual is
encouraged to develop a pers∞nal relati∞n with Æ∞n and
Sustainer through the pursuit of the knowλedge of reaλity in the hope
of curing the spiritual c✡rrupti✡n that has enveloped the human
spirit. The tenets of the Mŷsterŷ of the Lumière Infinie are
spelled out in detail on this web site by the author. Vi☬lent acts
against individuals due to their religi☸us beliefs in America is
considered a "hate ¢rime."
This web site in no way
c☬nd☬nes vi☬lence. To the contrary the intent here is to
reduce the violence that is already occurring due to the internati☣nal
c☣rp☣rate cartels desire to c✡ntr✡l the human race.
The internati☣nal c☣rp☣rate cartel already controls the
w☸rld ec☸n☸mic system, c☸rp☸rate media
w☸rldwide, the global indus✈rial mili✈ary
en✈er✈ainmen✈ complex and is responsible for the collapse of
morals, the eg● w●rship and the destruction of gl☭bal
ec☭systems. Civilization is based on coöperation. Coöperation
with bi☣hazards at the point
of a gun.
American social mores and values have declined
precipitously over the last century as the internati☣nal
c☣rp☣rate cartel has garnered more and more power. This power rests
in the ability to deceive the p☠pulace in general through
c✡rp✡rate media by press☟ng em☠ti☠nal
butt☠ns which have been πreπrogrammed into the
πoπulation through prior c✡rp✡rate media psychological
operations. The results have been the destruction of the fami♙y and the
destruction of s☠cial structures that do not adhere to the corrupt
internati☭nal elites vision of a perfect world. Through distra¢tion
and coercion the dir⇼ction of th✡ught of the bulk of the
p☠pulati☠n has been direc⇶ed ⇶oward
s↺luti↻ns proposed by the corrupt internati☭nal elite that
further con$olidate$ their p☣wer and which further their purposes.
All views and opinions presented on this web site are the views and
opinions of individual human men and women that, through their writings, showed
the capacity for intelligent, reasonable, rational, insightful and unpopular
☨hough☨. All factual information presented on this web site is
believed to be true and accurate and is presented as originally presented in
print media which may or may not have originally presented the facts
truthfully. Øpinion and
☨hough☨s have been adapted, edited, corrected, redacted, combined,
added to, re-edited and re-corrected as nearly all opinion and
☨hough☨ has been throughout time but has been done so in the spirit
of the original writer with the intent of making his or her
☨hough☨s and opinions clearer and relevant to the reader in the
present time.
Fair Use Notice

This site may contain
copyrighted material the use of which has not always been specifically
authorized by the copyright owner. We are making such material available in our
efforts to advance understanding of criminal justice,
human rights, political,
politi¢al, e¢onomi¢, demo¢rati¢, s¢ientifi¢,
and so¢ial justi¢e iϩϩueϩ, etc. We believe this
constitutes a 'fair use' of any such copyrighted material as provided for in
section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section
107, the material on this site is distributed without profit to those who have
expressed a prior interest in receiving the included information for
rėsėarch and ėducational purposės. For more information
see: www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted
material from this site for purposes of your own that go beyond 'fair use', you
must obtain permission from the copyright owner. |
 Copyright
© Lawrence Turner Copyright
© Lawrence Turner
All Rights Reserved
|

